Key findings
- DDoS attacks surged by 121% in 2025, reaching an average of 5,376 attacks automatically mitigated every hour.
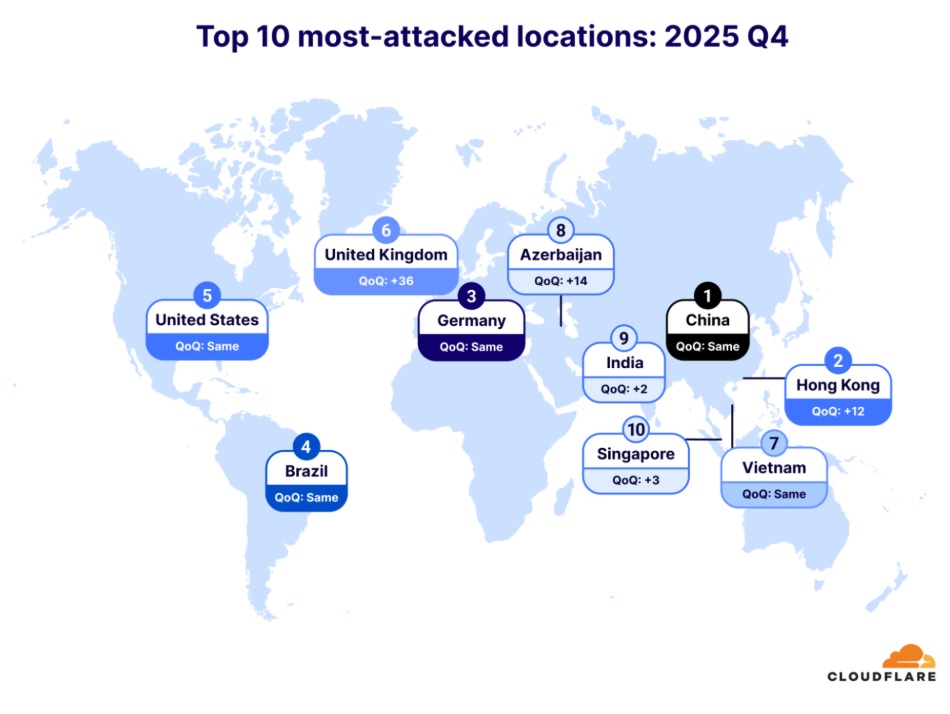
- In the final quarter of 2025, Hong Kong jumped 12 places, making it the second most DDoS’d place on earth. The United Kingdom also leapt by an astonishing 36 places, making it the sixth most-attacked place.
- Infected Android TVs — part of the Aisuru-Kimwolf botnet — bombarded Cloudflare’s network with hyper-volumetric HTTP DDoS attacks, while Telcos emerged as the most-attacked industry.
Cloudflare, Inc. has announced its 2025 Q4 DDoS report. This report offers a comprehensive analysis of the evolving threat landscape of Distributed Denial of Service (DDoS) attacks based on data from the Cloudflare network, which is one of the largest in the world.
2025 saw a huge spike in DDoS attacks
In 2025, the total number of DDoS attacks more than doubled to an incredible 47.1 million. Such attacks have soared in recent years: The number of DDoS attacks spiked 236% between 2023 and 2025.
In 2025, Cloudflare mitigated an average of 5,376 DDoS attacks every hour — of these, 3,925 were network-layer DDoS attacks and 1,451 were HTTP DDoS attacks.

Network-layer DDoS attacks more than tripled in 2025
The most substantial growth was in network-layer DDoS attacks, which more than tripled year over year. Cloudflare mitigated 34.4 million network-layer DDoS attacks in 2025, compared to 11.4 million in 2024. In 2025 Q4, network-layer DDoS attacks accounted for 78% of all DDoS attacks.
“The Night Before Christmas” DDoS campaign
On Friday, December 19, 2025, the Aisuru-Kimwolf botnet began bombarding Cloudflare infrastructure and Cloudflare customers with hyper-volumetric DDoS attacks. What was new in this campaign was its size: The botnet used hyper-volumetric HTTP DDoS attacks exceeding rates of 20 million requests per second (Mrps). The Aisuru-Kimwolf botnet is a massive collection of malware-infected devices, primarily Android TVs. The botnet comprises an estimated 1-4 million infected hosts. It is capable of launching DDoS attacks that can cripple critical infrastructure, crash most legacy cloud-based DDoS protection solutions, and even disrupt the connectivity of entire nations.
While highly dramatic, The Night Before Christmas campaign accounted for only a small portion of the hyper-volumetric DDoS attacks seen throughout the year.
Hyper-volumetric DDoS attacks
Throughout 2025, Cloudflare observed a continuous increase in hyper-volumetric DDoS attacks. In 2025 Q4, hyper-volumetric attacks increased by 40% compared to the previous quarter. As the number of attacks increased over the course of 2025, the size of the attacks increased as well, growing by over 700% compared to the large attacks seen in late 2024, with one reaching 31.4 Tbps in a DDoS attack that lasted just 35 seconds.
Most attacked industries
When analyzing DDoS attacks of all sizes, the Telecommunications, Service Providers and Carriers industry was the most targeted, followed by Information Technology & Services. The Gambling Casinos and Gaming industries ranked third and fourth, respectively and Computer Software at number five.
Most-attacked locations
The DDoS landscape saw both predictable stability and dramatic shifts among the world’s most-attacked locations. Targets like China, Hongkong, Germany, Brazil, and the United States were the top five, demonstrating persistent appeal for attackers.
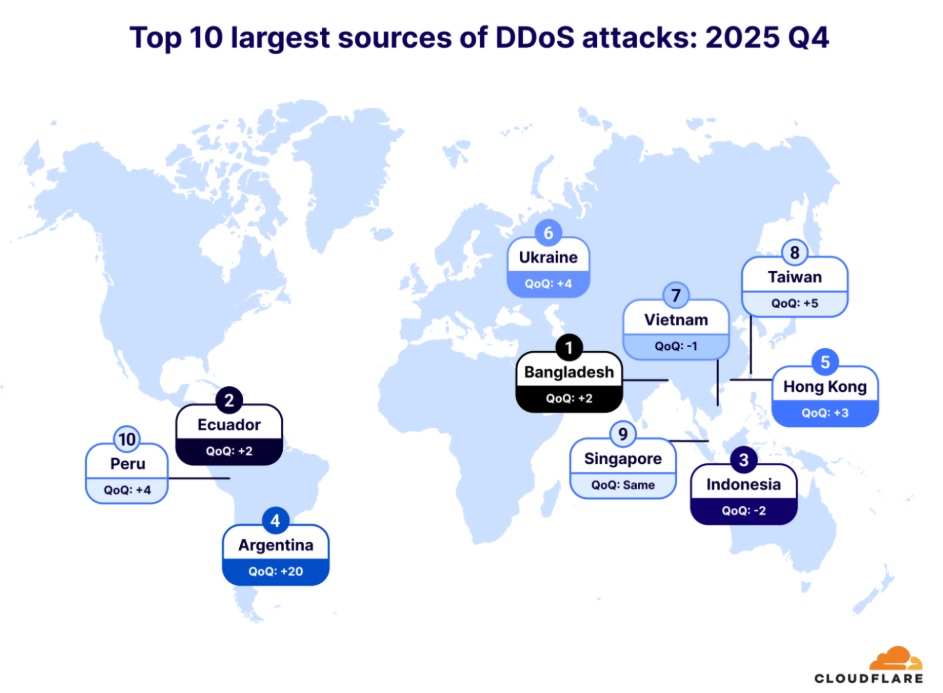
Top attack sources
Bangladesh dethroned Indonesia as the largest source of DDoS attacks in the fourth quarter of 2025. Indonesia dropped to the third spot, after spending a year as the top source of DDoS attacks. Ecuador also jumped two spots, making it the second-largest source.
Commenting on the report, Ercan Aydin, AVP, Middle East, Türkiye & Africa, at Cloudflare, says, “The scale and frequency of DDoS activity we observed in 2025 underscore how quickly threat actors are evolving their tactics. From hyper-volumetric attacks that set new records in bandwidth to complex, multi-vector campaigns, our data shows that safeguarding digital services requires adaptive, autonomous defenses. This is especially true across the Middle East, Türkiye, and Africa, where critical infrastructure and enterprise digital adoption are accelerating. By proactively leveraging real-time intelligence and mitigation capabilities, we help organisations stay ahead of these escalating threats.”
Top source networks
The top 10 list of attack source networks reads like a list of Internet giants, revealing a fascinating story about the anatomy of modern DDoS attacks. The common thread is clear:
- Threat actors are leveraging the world’s most accessible and powerful network infrastructure — primarily large, public-facing services.
- Most DDoS attacks coming from IP addresses associated with Cloud Computing Platforms and Cloud Infrastructure Providers, including DigitalOcean (AS 14061), Microsoft (AS 8075), Tencent (AS 132203), Oracle (AS 31898), and Hetzner (AS 24940). This demonstrates the strong link between easily-provisioned virtual machines and high-volume attacks.
- While the sheer scale of the highest-ranking sources often originates from global cloud hubs, the problem is truly worldwide, routed through the Internet’s most critical pathways from across the globe.


